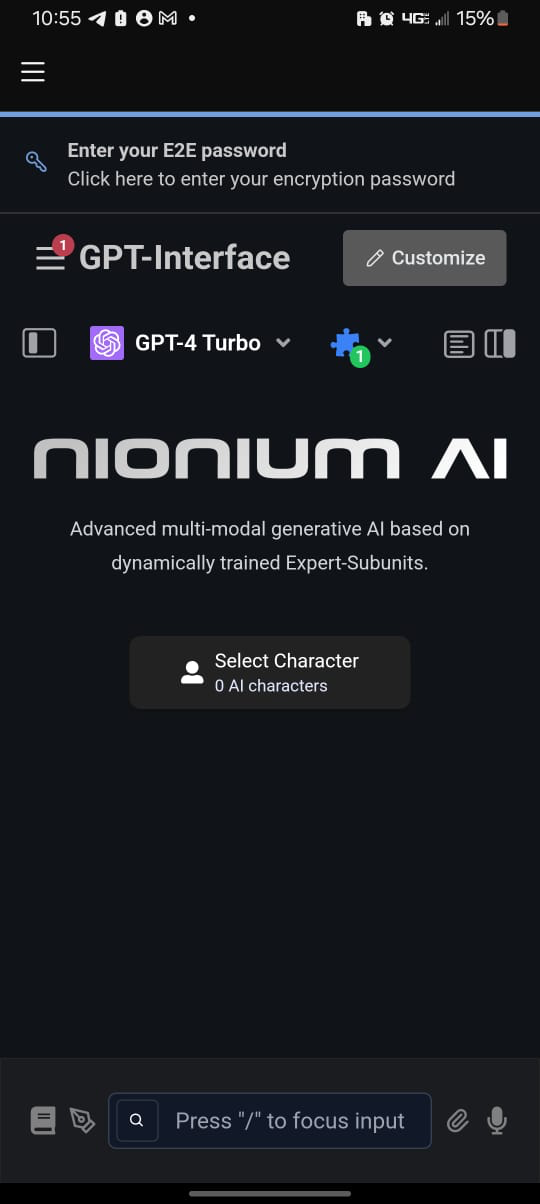
Military Grade AI-Enhanced Secure Communication for Tomorrow's Internet
- 7-Day Free Trial
- No Credit Card
Secure Communication is Essential
Plan, execute, and connect securely
with a team of any size
Our platform ensures advanced planning capabilities, encrypted collaboration, top-tier data protection, and AI-driven support for a seamless experience.
Real-time analytics
Encrypted Chat: Your Fortress of Privacy
Boost productivity, optimize workflows, and make data-driven decisions effortlessly.
- Symmetrical Key Encryption: AES-256 is a symmetrical key encryption algorithm, meaning it uses the same key for both encrypting and decrypting data. The key is a shared secret between the sender and receiver.
- Key Size: The “256” in AES-256 denotes the key size, which is 256 bits. This refers to the length of the secret key used for encrypting data. AES also comes in variants like AES-128 (128-bit keys) and AES-192 (192-bit keys), but AES-256 offers the highest level of security.
- Block Cipher: AES operates on fixed-size blocks of data, typically 128 bits. If a data piece doesn’t fit exactly into a 128-bit block, it must be padded to match this size.
- Number of Rounds: In the AES encryption process, data goes through multiple rounds of transformation. For AES-256, there are 14 rounds of processing involved. Each round consists of several steps that include substitution, transposition, and mixing of the input plaintext to transform it into the final output of ciphertext.
- Usage: AES-256 is used in numerous applications and protocols, including VPNs, SSL/TLS for secure web browsing, and file encryption tools. It’s selected for scenarios demanding high security due to its robustness against various attack vectors.
- Security: The U.S. National Institute of Standards and Technology (NIST) adopted AES in 2001. AES-256 is approved by the National Security Agency (NSA) for the protection of classified information up to the top-secret level, showcasing its high level of security.
- Performance: Despite its strong security features, AES-256 is designed to work efficiently both in software and hardware implementations. It can run smoothly on various platforms, including those with limited computational power.



Seamless workflows
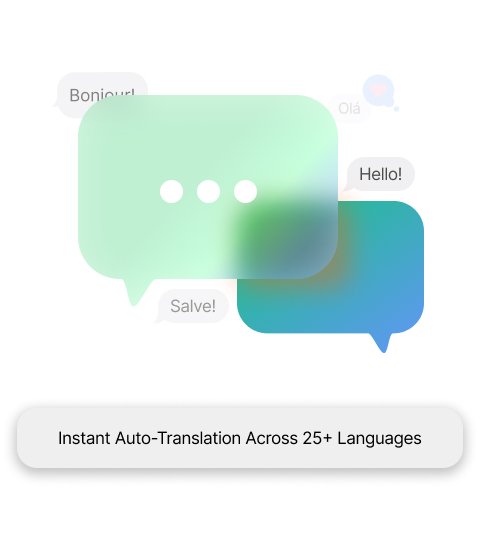
Transcending Language Barriers
Automate repetitive tasks, streamline processes, and enhance productivity with our powerful tools.
- Language Barriers Removed Auto-Translation
- DeepL Integration Superior translation quality. Best translation engine worldwide.
- Multi-Lingual Platform 24 Languages including Russian, Chinese and Japanese
Your Communication hub, accelerated
Streamline your project hub with our AI-enhanced platform, merging top-tier communication tools for unparalleled efficiency and connectivity.
-
Large file transfer redefined, Secure and Reliable
File Transfer -
You need a reliable backend application that is fast and scales
Collaboration -
Using an app that scales easily you don’t need to create
Workflow
Large File Transfer
up to 200 gb
Transcend limitations with the ability to send substantial documents or media files seamlessly, supported by our robust and secure transfer system


Collaboration tools
Built-in collaboration tools
shared documents
Facilitate collaborative efforts with built-in communication tools, shared documents, and team-specific workspaces.

Workflow tools
Automate your workflows
and put tasks on autopilot
Tailor your projects with customizable templates, fields, and dashboards, aligning the app with your unique workflow requirements.

Empowering innovative brands
Trusted by companies across industries
We work with diverse startups, spanning many sectors. Whatever industry you’re in, we’re here to partner with you and help you thrive.
Flexible pricing
Flexible pricing to suit every need
Enjoy a range of features designed to enhance your project management experience, all at a price that fits your budget.
Cipher Starter
For individuals or small teams
- Secure ChatGPT: Advanced AI-powered chat
- End-to-End Encryption: For texts, calls, and files ensuring your data remains confidential.
- File Security: Unlimited encrypted file transfers, including PDFs, images, and audio.
- Research Shield: In-depth encrypted research with comprehensive security layers.
- Prompt Secure: Enhances your security prompts for optimal protection.
- 50 generations per day
Enigma Pro
For individuals or small teams
- Secure ChatGPT: Advanced AI-powered chat
- End-to-End Encryption: For texts, calls, and files ensuring your data remains confidential.
- File Security: Unlimited encrypted file transfers, including PDFs, images, and audio.
- Research Shield: In-depth encrypted research with comprehensive security layers.
- Prompt Secure: Enhances your security prompts for optimal protection.
- unlimited secure generations
Enterprise
Ideal For large businesses and enterprises
- Everything from Enigma Pro plus:
- Real-time analytics, a dedicated account manager, and API access
- Project management capabilities and strategic decision-making
- Users can manage unlimited projects
Cipher Starter
For individuals or small teams
- Secure ChatGPT: Advanced AI-powered chat
- End-to-End Encryption: For texts, calls, and files ensuring your data remains confidential.
- File Security: Unlimited encrypted file transfers, including PDFs, images, and audio.
- Research Shield: In-depth encrypted research with comprehensive security layers.
- Prompt Secure: Enhances your security prompts for optimal protection.
- 50 generations per day
Enigma Pro
For individuals or small teams
- Secure ChatGPT: Advanced AI-powered chat
- End-to-End Encryption: For texts, calls, and files ensuring your data remains confidential.
- File Security: Unlimited encrypted file transfers, including PDFs, images, and audio.
- Research Shield: In-depth encrypted research with comprehensive security layers.
- Prompt Secure: Enhances your security prompts for optimal protection.
- unlimited secure generations
Enterprise
Ideal For large businesses and enterprises
- Everything from Enigma Pro plus:
- Real-time analytics, a dedicated account manager, and API access
- Project management capabilities and strategic decision-making
- Users can manage unlimited projects
Customer Testimonials
Don't take our word for it
The best way to showcase our commitment is through the experiences and stories of those who have partnered with us.
This software simplifies the website building process, making it easy and fast to manage our online presence.







Frederic Hill
Founder & CEO
Increase in ad awareness in the first month
This software simplifies the website building process, making it easy and fast to manage our online presence.







Frederic Hill
Founder & CEO
Increase in ad awareness in the first month
This software simplifies the website building process, making it easy and fast to manage our online presence.







Frederic Hill
Founder & CEO
Increase in ad awareness in the first month
This software simplifies the website building process, making it easy and fast to manage our online presence.







Frederic Hill
Founder & CEO
Increase in ad awareness in the first month
This software simplifies the website building process, making it easy and fast to manage our online presence.







Frederic Hill
Founder & CEO
Increase in ad awareness in the first month
This software simplifies the website building process, making it easy and fast to manage our online presence.







Frederic Hill
Founder & CEO
Increase in ad awareness in the first month
We've got answers
Your questions answered
If you're new or looking for answers to your questions, this guide will help you learn more about our services and their features.
A single, powerful, easy-to-use platform